Ken McLaurin, Senior Manager, Product Strategy, Red Hat Data flowing from an Internet of Things (IoT) solution can be its biggest asset and the biggest problem. Since IoT devices do not perform in the traditional server/client model - communication takes place in an orderly manner in the model - the IoT must be designed with the explicit goal of ensuring data integrity. This is a complex challenge that spans all phases of equipment, communication paths, and data collection, transmission, and analysis. In this article we will examine how to manage this complexity with a multi-tier architecture. We will consider what data integrity is required at each layer and how it meets the relevant requirements. Finally we will describe how solutions based on Intel® processors and Red Hat software simplify the deployment by scaling between each layer of requirements. IoT solutions vary greatly, but they all derive value from sharing information. Broadly speaking, IoT solutions collect data from edge devices, transmit it to the cloud, and analyze it to control edge devices. Because data is often collected and operated immediately, data integrity does not only mean protecting data. It means transmitting the right data in the right order and with the right security at the right time. Considering the train signal system, the train transmits position and data data to equipment next to the railway and important dispatchers. These data are critical to safety and enable functions such as train control (PTC). Hijacking and manipulating this type of data can lead to disasters, and the order in which data is received and acted upon is also a simple matter. Improperly sorted information can lead to command overrides and other processing issues. Ensuring data integrity in such systems requires a comprehensive solution that extends from the edge to the cloud. This poses several challenges, such as determining how to distribute data processing responsibilities in a networked system. One approach is to use a multi-tier architecture consisting of a device layer, a gateway layer, and a data center layer. Figure 1 shows how to allocate data processing activities in this architecture. Allocating data activities more clearly describes system requirements in terms of physical characteristics, computational requirements, bandwidth and latency, and security. Figure 2 illustrates some of the unique data processing requirements for each layer. Because of the distributed data activity, each layer has unique computational requirements. The scalability of Intel processors plays an important role here. Intel processors meet the requirements of each tier, providing a consistent architecture while ensuring that any tier will not be underutilized or resource intensive. This scalability also enables consistency in operating systems (OS), communication and application infrastructure settings, and development tools. A code set can work between layers to simplify each build and maintenance phase of the IoT solution. Let's consider how these processors meet the important needs of each layer: Equipment – The primary responsibility of this layer is to collect data and control equipment operations. The challenge is to strike a balance between tight power and size constraints and resource requirements. The Intel® QuarkTM SoC X1000 provides ready answers with typical power consumption of only 1.5W and high I/O and network integration levels in a 15mm x 15mm package. Its 400 MHz core provides significant performance for low latency collection and manipulation of data. Secure Boot ROM and other functions help to solve system integrity. For devices with greater processing needs – such as complex motion control or HD digital signage – Intel offers higher performance options such as the Intel® AtomTM processor E3800 product family. Gateways - Gateways can address bottlenecks that hamper enterprise-wide solutions by reducing data center load by preprocessing data (through aggregation and aggregation), relaying data, and controlling devices according to business rules. Gateways also play a key role in data security and perform tasks such as encryption and decryption. Since gateways are usually located close to the equipment, they also help to solve delay problems and shorten the data round trip distance. Gateway requirements span a wide range, depending on market segmentation and application. The Intel® Internet of Things addresses these very different needs. This gateway series scales from the Intel Quark SoC X1000 to the Intel Atom processor E3800 product family, offering I/O options for industrial, energy, transportation, retail, and other applications. The Intel Quark SoC X1000 flexibly addresses gateway space and energy constraints that have these concerns. For gateways that require more resources, the Intel Atom processor E3800 product family is ideally suited to provide power-efficient quad-core performance, as well as robust memory and rich LAN/WAN connectivity. These processors also provide advanced security features, including Secure Boot, Intel® AES New Instructions for hardware-assisted encryption/decryption (Intel® AES-NI), and Intel® Virtualization Technology (Intel® VT) - allowing critical applications and Less critical separation of code security. Data Center - The data center design can choose from a variety of processors depending on whether the goal is to scale up or down (or both). The Intel® Xeon® processor E5-2600 v3 series delivers exceptional performance for analysis with up to 24 cores in an embedded dual-core configuration – 20% more cores than the previous generation. (The platform also offers an enterprise-facing segment with up to 36 cores in a dual-core configuration.) The platform also provides enhanced virtual support and opens up important features in the hybrid cloud model. Intel's consistent architecture allows Red Hat to provide a unified platform for distributed IoT implementations. It starts with an operating system that can be configured and optimized for each layer. Layered data transmission and business rules technology at the top provide data connectivity and integrity. Equipment – The equipment needs a small-sized embedded operating system that provides strong security and performance. Red Hat Enterprise Linux provides these features in operating systems that scale from enterprise data centers to embedded solutions. Linux containers provide a lightweight, easy-to-maintain infrastructure for deploying applications on power-constrained devices. At the same time, Red Hat Enterprise Linux is Common Criteria EAL 4+ certified and provides military-grade security to prevent intrusion and protect data. To communicate with higher layers, developers can use Red Hat JBoss middleware. This middleware solves data acquisition and communication with products like Red Hat JBoss A-MQ. As shown in Figure 3, JBoss A-MQ provides a standards-based robust platform with high flexibility, reliability, and real-time performance. JBoss A-MQ asynchronous messages are often deployed where data integrity is important, such as PTC and air-to-ground information exchange systems. Gateway - The same Red Hat Enterprise Linux can serve this layer, connecting devices via JBoss A-MQ. Developers can use Red Hat JBoss Fuse in situations where multiple data formats need to be converted to standard format machine-to-machine (M2M) communications. This flexible, small-footprint Enterprise Service Bus (ESB) enables fast cross-system integration with features such as 150+ Apache Camel connectors. When the gateway needs to take action on data input, developers can use the small-sized Red Hat JBoss BRMS, a platform for business rules management and complex event processing (CEP). JBoss BRMS provides the same type of mature decision logic that typically resides in the data center. This logic can be constructed using simple metaphors (such as decision tables, scorecards, and domain-specific languages) through Web-based graphical tools. Red Hat Enterprise Virtualization enhances gateway security. Functions like sVirt and SELinux provide kernel-level protection for hypervisors and guests. These features help developers and administrators: • Protect multiple tenants • Quickly fix dangerous leaks • Protect data at rest and across the network • Reduce exposure with strict authority • Simplify auditing with completely separated guests • Use encryption to prevent malware attacks As mentioned earlier, Intel also provides its own software stack for Intel IoT gateways. The flexibility of the Red Hat solution allows these gateways to be integrated at any time in an end-to-end solution. Data Centers – Various Red Hat products play an important role here, such as Red Hat Storage Servers based on Gluster and Ceph, highly flexible and scalable software-defined solutions for phased big data deployments such as Hadoop and Cloudera installations. For the Open Hybrid Cloud data center, the Red Hat Enterprise Linux OpenStack Platform is provided, which is built on the same Red Hat Enterprise Linux found in other tiers (see Figure 4). This platform allows developers to smoothly transition part of a distributed processing architecture to the cloud. The Internet of Things is built with a range of devices and servers that can benefit from Intel processors. For on-site deployments, these processors provide an excellent balance between computing requirements and energy and space requirements. In the data center, they provide the ability to make full use of data flowing from the Internet of Things. Having hardware scaled throughout the IoT solution is critical to creating a consistent software architecture. Red Hat's IoT products offer scalability benefits by providing enterprise-wide solutions across all layers of the Internet of Things. Intel processors and Red Hat software together provide an attractive end-to-end IoT platform that completely addresses data integrity needs. Single Burner Electric Hotplate Portable Hot Plate,Single Burner Electric Hotplate,Hot Plates,Hot Plates With Stainless Housing Shaoxing Haoda Electrical Appliance Co.,Ltd , https://www.hotplates.nl
Data challenge 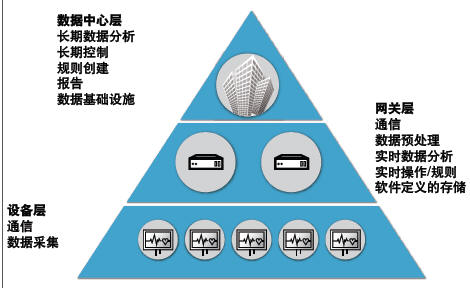
Figure 1. Data management can be distributed in a three-tier architecture. 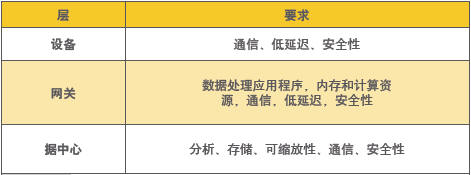
Figure 2. Each floor has unique requirements.
Processing requirements
Software solution 
Figure 3. Red Hat JBoss components provide a robust messaging framework. 
Figure 4. Red Hat Enteprise Linux OpenStack Platform
End-to-end solution