Aluminum Die Casting,Aluminum Die Casting Parts,Aluminium Die Casting Process,Aluminium Die Casting Dongguan Formal Precision Metal Parts Co,. Ltd , https://www.formalmetal.com
This article explains the concept of authentication and Maxim's solution to provide encryption control and protection in the form of secure memory, which is ideal for applications requiring intellectual property protection, HW / SW permission management, security software function and status settings, and tamper-resistant data storage.
What is authentication? Authentication refers to the process of establishing identity recognition between two or more entities. In the case of one-way authentication, one party needs to prove the legality of its identity to the other party. For two-way authentication, both parties need to prove their identity to each other. The most common authentication method is to use a password. The main problem with using passwords is that passwords in applications are exposed and can be easily detected.
Let ’s first review the historical application of encryption. In 1883, Flanders linguist Auguste Kerckhoffs published an article on military encryption, which shocked the entire world. Kerckhoffs preached that security should not rely on concealment (such as a non-public secret algorithm), but on the power of algorithms and their keys. If security is compromised, Kerckhoffs believes that only the key needs to be replaced, not the entire system.
The key-based authentication process is shown in Figure 1: The key (private) and the data to be authenticated ("information") are used as inputs to calculate the information authentication code, or MAC. The MAC is then attached to the information. The receiver of the information performs the same operation and compares the MAC calculation result with the MAC received with the message. If the two are the same, the information is legal. 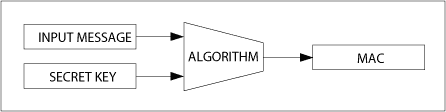
Figure 1. The MAC calculation model
However, this basic MAC calculation model also has a weakness. If the illegal person intercepts the information, he can then play back the information to impersonate his legal identity. To overcome this inherent MAC weakness and prove the legal identity of the MAC sender, the receiver can generate a random number and send it back to the sender as a challenge code. The MAC sender must recalculate the new MAC based on the key, information, and challenge code, and return it to the receiver. If the sender can generate a valid MAC corresponding to any challenge code, you can be sure that the sender knows the key and its identity is legal (Figure 2). This process is called challenge-response authentication. 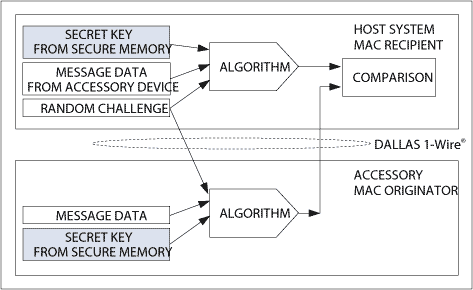
Figure 2. Challenge-response authentication process
In cryptography, the algorithm that generates a fixed-length MAC from information is called a "one-way" hash function. One-way means that it is extremely difficult to output long-form original information from a fixed-length MAC. On the contrary, through encryption, the encrypted information is proportional to the original information.
SHA-1 is a one-way hash algorithm that has been thoroughly researched and internationally recognized, and was developed by NaTIonal InsTItute of Standards and Technology (NIST). SHA-1 has developed into the international standard ISO / IEC 10118-3: 2004, and the mathematical basis of the algorithm is public and can be obtained from the NIST website. The main features of the SHA-1 algorithm include the following: 1) Irreversibility—from a computational perspective, it is impossible to derive input information from the MAC; 2) Anti-collision—for a specific MAC, it is not possible to find more than one input information Realistic; 3) High avalanche effect-any change in the input will cause a huge change in the MAC result. For these reasons and international research on the algorithm, Maxim chose SHA-1 as its challenge-response authentication algorithm for secure storage.
Low-cost safety certification-function realization
DS2432 EEPROM has a built-in SHA-1 engine. With the 1-Wire interface, it can be easily added to any circuit with digital processing capabilities, such as a circuit with a microcontroller (µC). In the simplest case, only a free I / O pin and a pull-up resistor are needed to form a 1-Wire interface, as shown in Figure 3. If the computing power on the board or the remaining program storage space is not enough to complete the SHA-1 MAC calculation, the designer can use the DS2460 SHA-1 coprocessor or transfer the calculation task to the nearest host in the system or network. The coprocessor also has another benefit. The system key can be stored in secure memory instead of being stored in the program code. 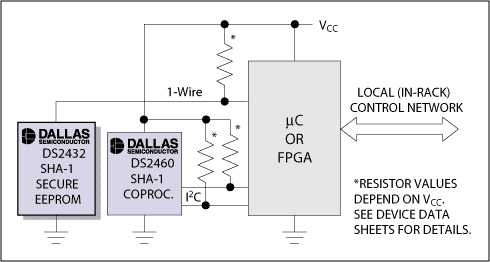
Figure 3. Typical system environment
The embedded hardware / software authorization management reference design requires authorization and may be produced by a third party and needs to be protected against illegal use of program code. Considering the revenue reasons, it is also necessary to track and confirm the number of times the reference design is used. The DS2432 is pre-programmed (the key and memory settings are loaded before being supplied to a third-party manufacturer) to easily meet these needs and provide more functions. At power-on self-test, the reference design (Figure 4) performs the certification process through the DS2432. Only DS2432 with a valid key can successfully return a valid MAC. If an invalid MAC is detected, the processor will take the corresponding specific action. This method also brings another benefit, that is, the function of the reference design can be selectively authorized and enabled through the setting value of the DS2432 secure memory. (For more information about this concept, see the section on software function management.)
DS2432 with a 64-bit valid key can be provided to authorized persons or third-party manufacturers through the following two security methods: a) pre-programmed by a reference design authorization company; or b) pre-programmed by Maxim based on the authorized company ’s input information and Supply to third-party manufacturers. Regardless of the method used, the number of devices supplied to the licensee or manufacturer is known, and the license fee can be charged accordingly. 
Figure 4. Certified reference design
Verifying the legality of the hardware When verifying the legality of the hardware, two cases need to be considered (Figure 5): 1) clone the circuit board to completely copy the firmware / FPGA configuration information; and 2) clone the system host. 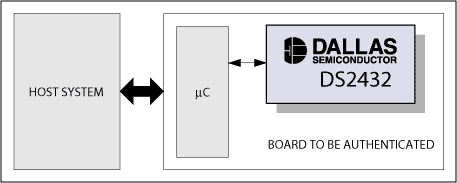
Figure 5. Example of hardware certification
In the first case, the firmware / FPGA attempts to authenticate the cloned circuit board. To write data to the user EEPROM, the clone manufacturer must load the key into the DS2432. Although this makes the data seem correct, the key is not valid in the system. Due to the complexity of changing firmware / FPGA, in order to maintain compatibility with the host, the original firmware / configuration information must be copied accurately. If the board performs the DS2432 challenge-response authentication process during the power-up phase, the MAC generated by the DS2432 is different from the MAC calculated by the microcontroller / FPGA. The MAC mismatch fully proves that the circuit board is illegal. The interrogation / response process between the system and the circuit board can detect this mismatch and take specific actions accordingly.
In the second case, the circuit board attempts to authenticate the host system. The circuit board verifies the identity of the host through the following steps: 1) Generate a challenge code, and the DS2432 calculates the challenge-response authentication code MAC; 2) Send the same input data to calculate the MAC (of course not including the key) to the network host, the host according to these data Calculate and return the challenge-response authentication code MAC with the key you own. If the MACs generated by the two are the same, the circuit board concludes that the host is legal. Of course, if the DS2432 and the network host have an agreement, they can also get the same MAC.
Software function management electronic products range from handheld products to rack-mounted units. The larger the unit size, the more expensive the development cost. In order to effectively control the cost, it is very beneficial to use some smaller subsystems (circuit boards) to build large-scale systems. Usually, not all functions of the subsystem are needed in the application. The most cost-effective way is not to remove these functions, but to keep the circuit board unchanged and only disable certain functions in the control software. But this method will create new problems: if a smart customer needs some fully functional systems, he can only buy a complete set of units and some less functional units. Through software copying, units with fewer functions can provide complete functions at a lower price, thus deceiving system suppliers.
The DS2432 on each subsystem circuit board can protect system vendors from this type of fraud. In addition to challenge-response authentication, the DS2432 can also store independent configuration information in its user EEPROM. The configuration data can prevent illegal tampering, and the system supplier has full control, which will be further explained in the data security section. The configuration information can be stored in the form of bitmap or codeword, which is completely determined by the system designer. According to actual needs, configuration information should be set as simple as possible. Because the DS2432 provides a convenient 1-Wire interface, the designer only needs to add a transistor and a detection point, as shown in Figure 6. You can write configuration information to the DS2432 through the detection point when the other parts of the circuit board are not powered on. The MOSFET isolates the DS2432 from other circuits. When the subsystem works normally, it will not interfere with the normal access of the DS2432. 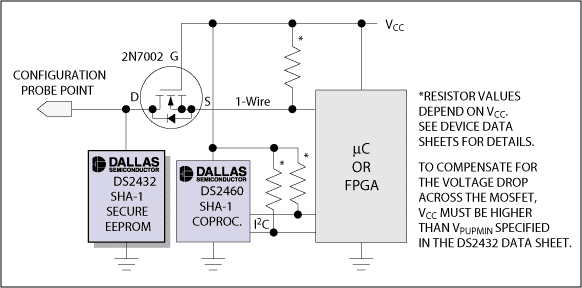
Figure 6. Add configuration probe points
This configuration writing method also brings another benefit. After the system is installed on the user's site, remote updates / changes are allowed. Any user EEPROM that is not used for configuration / function management can use the form of electronic signage to achieve circuit board identification. This feature is described in detail in Application Note 178: Using 1-Wire Product Identification Printed Circuit Boards. This application note 178 can be downloaded from the Maxim website.
DS2432 certification function details the overall architecture of the device
The main data unit and data flow path of DS2432 1-Wire interface, 1kb SHA-1 secure memory are shown in Figure 7. You can see the 8-byte key and the buffer memory (temporary memory) that temporarily stores the challenge code. Data units not mentioned previously include unique device ID numbers (standard 1-Wire features), four user EEPROM pages, control registers, and system constants.
The device ID is used as the node address in the 1-Wire network and also used in the authentication process. The user memory stores the main part of the "information" to be authenticated. The system constant helps to meet the format requirements and complete the filling function, thereby forming a 64-byte input data block for SHA-1 calculation. The control register performs specific device functions, such as optional key write protection or EEPROM emulation mode; the control register usually does not participate in the authentication process. 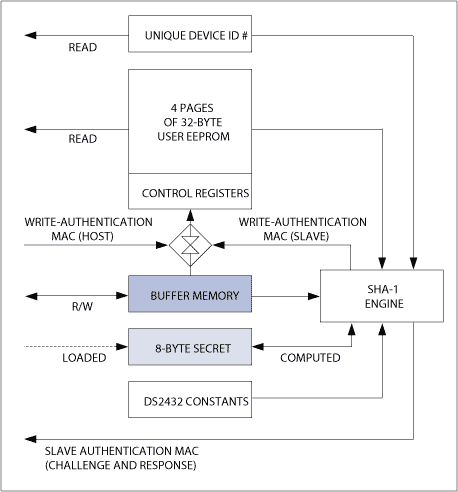
Figure 7. DS2432 SHA-1 secure memory data flow model
The device ID number and user EEPROM can be read without restriction. And can completely read / write access to the buffer memory. The key can be loaded directly, but it can never be read. Changing the contents of user memory or registers requires the master and slave (ie DS2432) to calculate the same authentication MAC for the write operation before the buffer memory to EEPROM path can be opened.
Depending on the different uses of the MAC result, the DS2432 SHA-1 engine has three different ways of working. In any case, the SHA-1 engine receives 64 bytes of input data and calculates a 20-byte MAC result. The difference is in the input data. As a fundamental requirement of a security system, the host must either know or be able to calculate the key of a valid / legal slave device in the application.
Challenge-response authentication MAC
As mentioned in the previous application examples, the main function of the DS2432 is to complete challenge-response authentication. The host sends a random challenge code, instructing the DS2432 to calculate the response MAC based on the challenge code, the key, the data of the memory page selected by the host, and other data (these data together constitute information) (see Figure 8). 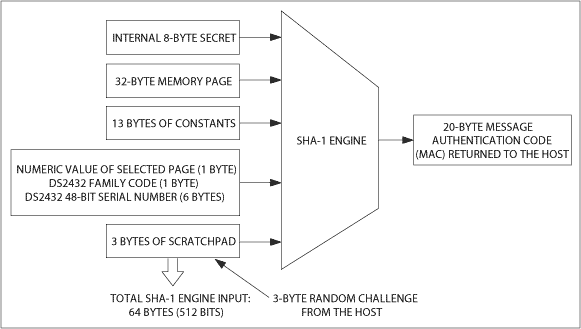
Figure 8. Used to generate challenge-response authentication MAC
After the DS2432 completes the calculation, it sends the MAC back to the host for verification. The host uses a valid key and the same information data used by the DS2432 to recalculate the MAC. If the result matches the MAC given by the DS2432, the device is legal because only the legitimate DS2432 can respond to the challenge-response process correctly. It is very important that the challenge code is random data. If the challenge code remains the same, it is vulnerable to a replay attack using a valid, static, recording and playback MAC (not the MAC calculated in real time using the certified DS2432).
In addition to providing the authentication function of the slave device, data security also strongly requires that the data stored in the device is reliable. To achieve this, the DS2432's write access is securely restricted. Before copying data from the scratchpad to the EEPROM or control register, the DS2432 requires the host to provide a write access authentication MAC to prove its legal identity. The DS2432 calculates the MAC based on the new data in the scratchpad, the key, the memory page data that needs to be updated, and other data (Figure 9).
The legitimate host knows the key and can calculate a valid write access MAC. When the host MAC is received during the execution of the copy command, the DS2432 compares it with the result of its calculation. Only when the two match, the data will be transferred from the buffer memory to the target EEPROM. Of course, write-protected memory pages cannot be modified, even if the MAC is correct. 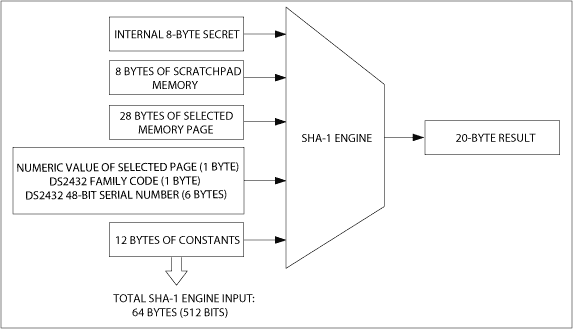
Figure 9. Input data used to calculate the MAC for write access authentication
Key protection
The DS2432's architecture allows keys to be loaded directly into the device. Key protection can be provided through read protection, and if necessary, write protection can also be used to provide key protection, which will never change the key. This level of protection is effective as long as the access key is secure and controllable at the equipment manufacturing site.
Different methods can be used to improve the key protection level: a) The DS2432 calculates its key; b) The DS2432 calculates its key in stages on different occasions; c) When calculating the key, it contains a unique device ID number, which is related to the device Key; d) Combine the second and third methods.
If the first method above is used, each DS2432 calculates its own key and only knows the original data of the calculated key; the key itself will never be exposed. If the second method is adopted, the key is calculated in stages on different occasions, and only the "local" original data of the key is known. This method can effectively control the "final" key information. If the key is related to the device (the third method), the host also needs to add a calculation step. But if the key of a device is accidentally discovered, the potential harm can be minimized. If the key is calculated in stages and related to the specific device (method 4), the highest protection level can be obtained. However, to ensure system confidentiality, the master and slave need to be set up in different locations.
Before calculating the key, a known value must be loaded as the key. With this known key, 32 bytes of data to calculate the new key must be written to one of the four memory pages. Next, you need to write a local key to the DS2432's scratchpad. The local key can be a memory page number used for calculation and a unique device ID number (except CRC bytes), or any other 8-byte data related to the application.
If the DS2432 is instructed to calculate the key, the DS2432 starts the SHA-1 engine and uses the input data shown in FIG. 10 to calculate the MAC. The lowest 8 bytes of the 20-byte MAC are automatically copied to the key memory address and immediately become a valid key. 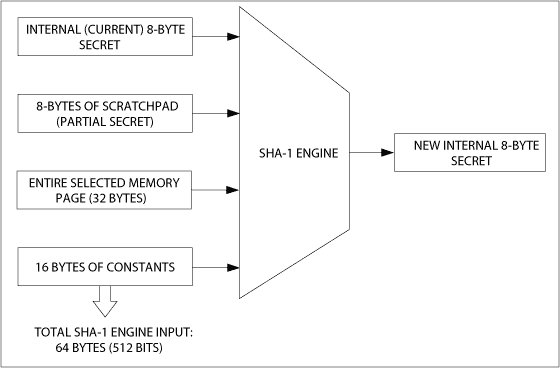
Figure 10. Input data for calculating the key
Conclusion Understanding and authentically implementing security authentication functions can provide a very competitive advantage. The certification not only protects the program code, but the public hardware platform uses secure software function settings to help reduce production costs. The data security of DS2432 can even realize remote configuration modification, saving valuable time for technicians. It can be seen from the functions demonstrated by the DS2432 that a small silicon wafer will have a huge impact on revenue.
Protect your research and development achievements-two-way authentication and software function protection
Abstract: In an age of impersonation and forgery of documents, it is essential to ensure correct identification. This is true not only for individuals, but also for electronic products. System vendors need to protect the safety of their products in environments where there is an "external hazard" such as a hacker attack and an "internal worry" such as cloning hardware. The key to achieving these security requirements is certification.