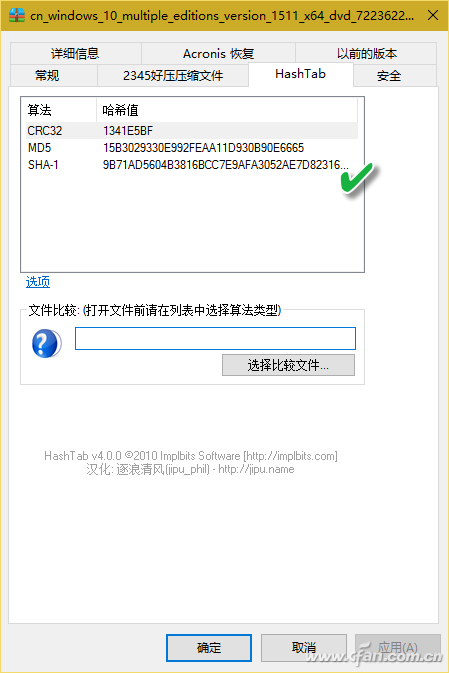
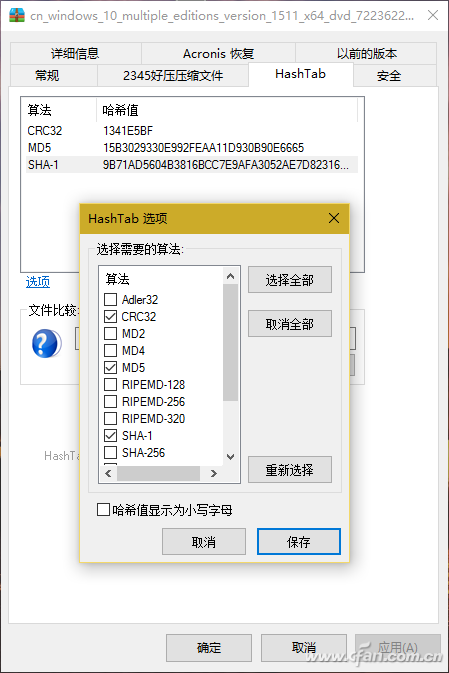
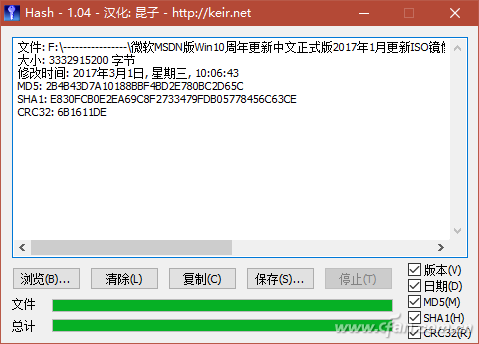
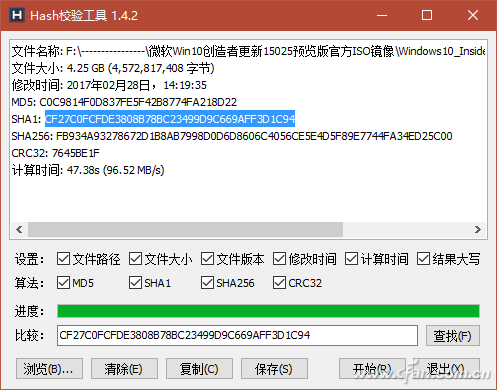
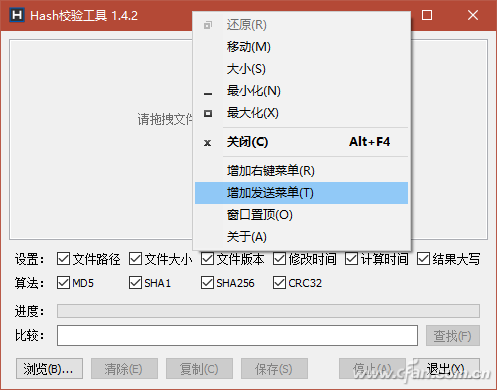
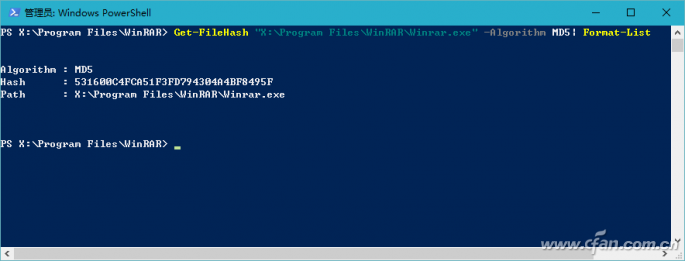
On some software download pages, such as the Microsoft Windows 10 download link page provided by Microsoft's MSDN subscription site, we often see code such as SHA1, MD5, CRC32 (Figure 1). These codes are used to verify the file download before and after The file check code used for consistency. By means of this verification file, it is possible to identify whether the software is entrained with "private goods" to prevent the software from being implanted with malicious software or even profitable bundled installation tools. File verification often refers to the process of verifying the consistency of a file on a website and a file after downloading using one or more checksums such as MD5, SHA1, CRC32 values, and the like. The check code is generally composed of a string of several lengths. These check codes composed of strings are calculated by the verification program from the contents of the file. Therefore, as long as the content of the file is fixed, the checksum will naturally be a fixed string. In the same way, if the file is modified, or there is a packet loss or error during the download and transmission, the verification code of the downloaded or received file will naturally change. For example: Microsoft's website gives the Windows 10 trial version of the ISO check code, and a system site also provides Microsoft's version of the system ISO download, but we are worried about whether this site provides Microsoft original ISO, then you can use to download to The ISO generated checksums are checked against the checksums provided by Microsoft. If they match, the downloaded ISOs are the original ones. Below we describe several practical methods for generating and verifying file verification data. Right-click property view If you often need to verify the file, you can install the checksum program HashTab 4.0 for Windows. After installation, the property verification function will be integrated into the file properties menu window. When you right-click a file and select "Properties", a HashTab tab will be added to the properties window and the progress of verifying the file will be displayed. Bar (Fig. 2); According to the length of the file, after waiting for different times, three different check values ​​are displayed in the algorithm and hash list window (Figure 3). Although the algorithm that the file checker displays by default is only the three types shown in the figure, in fact, the check algorithm included in the software is not limited to these three types. By right-clicking the list of hash values ​​and selecting the Enter Options window, you can choose from more than a dozen other algorithms (Figure 4). hint: If you want to give the check value before the file is online, you can use this method to generate the check code and paste it on the Internet. Similarly, after the file is downloaded, this method can also be used to obtain the check code. Compared with the check code given on the Internet, the consistency of the file content can be known. Drag to calculate attribute method If you do not use file verification often, there is no need to add plug-ins to the file right-click attributes to increase the burden. Just use a green check software Hash_V1.04, drag the file to be verified to the software window, and automatically generate MD5, SHA1, and CRC32 checksums (Figure 5). After verification, the check value can be conveniently saved by using the "copy" and "save" buttons. In addition, another similar software, Hash Verification Tool V1.4.2, is used to generate a more sophisticated SHA256 check in addition to the above three test values. With this software, multiple files or folders can be dragged and dropped into the window at one time for verification. At the same time, hash value strings can be searched. If there are many files for verification at one time, this function can be used to quickly find the corresponding file. The check code or a check code corresponds to the file (Figure 6). hint: Hash verification tool V1.4.2 version hidden in the add "right-click menu", "send menu", "window sticking top" and other functions, can achieve more convenient operation. Simply right-click on the software title bar and select it from the popup menu (Figure 7). 3. Use PowerShell to verify the file In Windows 10, file verification can also be performed via PowerShell window commands. PowerShell's default command line "Get-FileHash File Path | Format-List" gives the file's SHA256 checksum. If you use the "Get-FileHash file path-Algorithm verify content | Format-List" command, replace the "validation content" with SHA1, MD5 and other forms, you can give the corresponding type of checksum (Figure 8). Note that the space in the file path requires half-width quotation marks, and PowerShell file verification does not support CRC32.
Travel Charger Adapter is convenience for these people who always travel in many countries. Desktop Power Adapter have normal DC connector for your need, and wall power adapter have mutil plug, like US/UK/AU/EU etc. We also can produce the item according to your specific requirement. The material of this product is PC+ABS. All condition of our product is 100% brand new.
Our products built with input/output overvoltage protection, input/output overcurrent protection, over temperature protection, over power protection and short circuit protection. You can send more details of this product, so that we can offer best service to you!
Travel Charger Adapter,Portable Travel Charger Adapter,Mini Travel Charger Adapter,Travel Charger Supply Shenzhen Waweis Technology Co., Ltd. , https://www.szwaweischarger.com